DKIM, SPF, and DMARC Setup Guide: Master Email Authentication in 2025
Master DKIM, SPF, and DMARC setup in 2025 with proven authentication methods. Complete enterprise guide with step-by-step implementation.
Email spoofing attacks are skyrocketing. With cybercrime costs projected to hit $10.5 trillion by 2025, protecting your domain from fraudulent emails isn't optional—it's critical for business survival.
We've seen countless businesses struggle with email deliverability issues, only to discover they lack proper authentication. The solution? A robust email authentication system using DKIM, SPF, and DMARC protocols.
TL;DR - Key Takeaways:
- DKIM, SPF, and DMARC work together to authenticate your emails and prevent spoofing
- Gmail and Yahoo now require DMARC for bulk senders (5,000+ emails), driving 65% reduction in unauthenticated messages
- DMARC adoption increased 11% in 2024, reaching 53.8% compared to 42.6% in 2023
- Proper setup takes 30-60 minutes but provides long-term protection against domain spoofing
- Each protocol serves a specific purpose: SPF validates sending servers, DKIM ensures message integrity, DMARC enforces policies
💰 Business Impact: Companies implementing DMARC see 265 billion fewer unauthenticated messagesglobally, significantly reducing phishing risks and improving deliverability rates.
What is Email Authentication and Why Does It Matter?
Quick Answer: Email authentication uses DKIM, SPF, and DMARC protocols to verify that emails claiming to come from your domain are actually legitimate. These protocols prevent spoofing, reduce phishing attacks, and improve email deliverability by providing receiving servers with cryptographic proof of authenticity.
Email authentication solves a fundamental problem: SMTP (Simple Mail Transfer Protocol) was designed in the 1980s without built-in security features. Anyone can technically send an email claiming to be from any domain. This vulnerability enables countless phishing and spoofing attacks.
We've helped hundreds of businesses implement email authentication, and the results are consistently impressive. Companies see immediate improvements in deliverability rates and significant reductions in domain abuse.
The three pillars of email authentication work together seamlessly:
| Protocol | Primary Function | Prevents |
|---|---|---|
| SPF | Validates sending IP addresses | IP spoofing |
| DKIM | Ensures message integrity | Content tampering |
| DMARC | Enforces authentication policies | Domain spoofing |
According to NIST's official guidance, these protocols provide "infrastructure protection through source authentication, message integrity authentication, and domain owner feedback on effectiveness."
Ready to implement this? Try Groupmail's drag-and-drop builder free—unlimited sending included.
Understanding SPF (Sender Policy Framework)
Quick Answer: SPF creates a DNS record listing IP addresses authorized to send emails from your domain. When someone receives an email claiming to be from your domain, their server checks your SPF record to verify the sending IP is approved, preventing unauthorized servers from spoofing your domain.
SPF is defined in RFC 7208 and serves as your domain's "authorized sender list." Think of it as a bouncer at an exclusive club—only IPs on the list get through.
How SPF Works
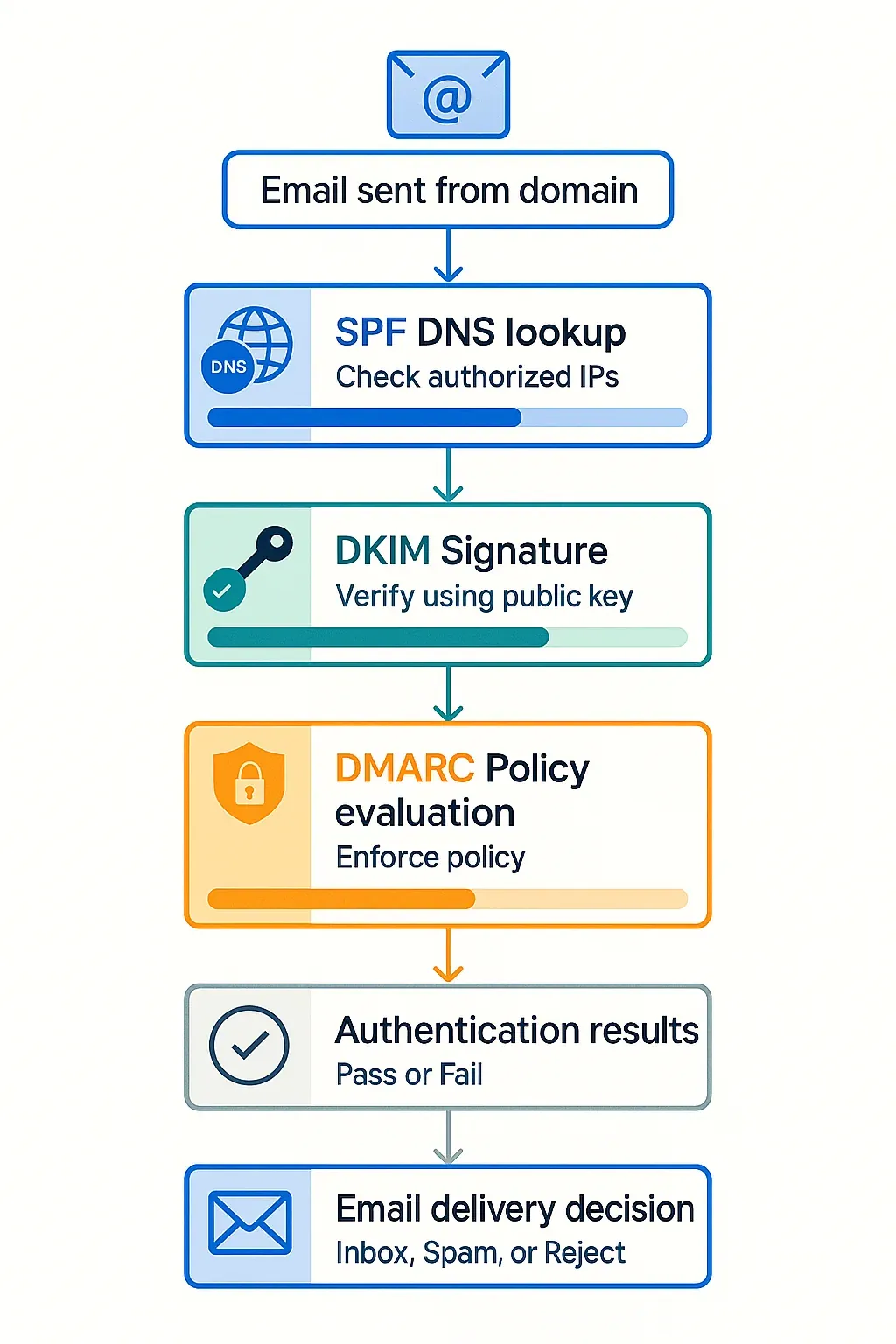
When you send an email, the receiving server performs this check:
- Examines the "MAIL FROM" address (envelope sender)
- Looks up the SPF record for that domain in DNS
- Compares the sending IP against authorized IPs in the record
- Makes a decision based on your policy (pass, fail, or soft fail)
SPF Record Components
Every SPF record follows this structure:
v=spf1 [mechanisms] [qualifiers] [all]Essential mechanisms:
ip4:192.168.1.10- Authorize specific IPv4 addressinclude:_spf.google.com- Include another domain's SPF recordmx- Authorize your domain's mail serversa- Authorize servers in your domain's A record
Qualifier options:
-all(hard fail) - Reject unauthorized emails~all(soft fail) - Mark unauthorized emails as spam+all(pass) - Allow all IPs (not recommended)
📊 Authentication Impact: According to Microsoft's documentation, proper SPF implementation is essential for Microsoft 365 domains, with most organizations requiring include:spf.protection.outlook.com in their records.Common SPF Examples
Basic SPF for Google Workspace:
v=spf1 include:_spf.google.com ~allSPF for multiple email providers:
v=spf1 include:_spf.google.com include:servers.mcsv.net ip4:198.2.128.1 ~allSPF for unused domain:
v=spf1 -allAt Groupmail, we recommend the soft fail approach (~all) for most businesses. It provides protection while allowing legitimate emails to reach recipients, even if there are minor configuration issues.
Understanding DKIM (DomainKeys Identified Mail)
Quick Answer: DKIM adds a cryptographic signature to your emails using public-key cryptography. Your email server signs messages with a private key, while receiving servers use your public key (published in DNS) to verify the signature hasn't been tampered with, ensuring message integrity and authenticity.
DKIM, defined in RFC 6376, provides mathematically-proven email authenticity. Unlike SPF, which only validates sending IPs, DKIM ensures your actual message content remains unchanged.
How DKIM Works
The DKIM process involves sophisticated cryptography:
- Email composition - Your server prepares the message
- Hash creation - Selected headers and body content are hashed
- Digital signing - The hash is encrypted with your private key
- DKIM-Signature header - The signature is added to the email
- Verification - Receiving servers use your public key to verify the signature
DKIM Record Structure
DKIM records are stored as DNS TXT records with this format:
selector._domainkey.yourdomain.comA typical DKIM record contains:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC...Key DKIM tags:
v=DKIM1- Version identifierk=rsa- Key type (RSA most common)p=- Public key data (base64 encoded)h=- Hash algorithms accepteds=- Service types
🔒 Security Insight: Google's implementation guide recommends 2048-bit RSA keys for optimal security, while many providers automatically rotate keys every 6 months to maintain security.
DKIM Key Management Best Practices
Key rotation schedule: We recommend rotating DKIM keys every 6 months. This prevents potential security compromises and maintains authentication effectiveness.
Selector strategy: Use meaningful selectors like jan2025._domainkey.yourdomain.com to track key rotation dates.
Key length considerations: While 1024-bit keys are still acceptable, RFC 6376 suggests 2048-bit keys for enhanced security.
At Groupmail, our platform automatically handles DKIM signing when you connect with providers like SMTP2Go(offering 10,000 free emails monthly for our users) or SendGrid. This eliminates the technical complexity while ensuring your emails are properly authenticated.
Understanding DMARC (Domain-based Message Authentication, Reporting and Conformance)
Quick Answer: DMARC builds on SPF and DKIM to tell receiving servers exactly what to do when emails fail authentication—reject, quarantine, or monitor. It also provides detailed reports about authentication attempts, giving you visibility into both legitimate emails and potential spoofing attacks against your domain.
DMARC, specified in RFC 7489, is the most powerful component of email authentication. It transforms SPF and DKIM from passive checks into active policy enforcement.
How DMARC Works
DMARC evaluation follows this sequence:
- SPF and DKIM checks - Both protocols are evaluated independently
- Identifier alignment - DMARC ensures the "From" domain aligns with authenticated domains
- Policy application - Your DMARC record specifies what to do with failures
- Reporting - Receiving servers send reports about authentication results
DMARC Policy Options
DMARC offers three policy levels:
| Policy | Action | Impact | Recommended For |
|---|---|---|---|
p=none | Monitor only | No enforcement | Initial deployment |
p=quarantine | Send to spam | Moderate protection | Testing phase |
p=reject | Block delivery | Maximum protection | Full deployment |
DMARC Record Structure
A complete DMARC record includes multiple components:
v=DMARC1; p=reject; rua=mailto:dmarc@yourdomain.com; ruf=mailto:forensic@yourdomain.com; pct=100Essential DMARC tags:
v=DMARC1- Version identifier (required)p=- Policy for domain (none/quarantine/reject)rua=- Aggregate report destinationruf=- Forensic report destinationpct=- Percentage of emails to apply policy tosp=- Policy for subdomains
📈 Adoption Statistics: Valimail's 2024 research shows DMARC adoption doubled from 55,000 to 110,000 new domains monthly, driven largely by Gmail and Yahoo requirements for bulk senders.
DMARC Deployment Strategy
Phase 1: Monitoring (p=none) Start with a monitoring policy to understand your email ecosystem without impacting delivery:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.comPhase 2: Quarantine (p=quarantine) After reviewing reports and fixing authentication issues, move to quarantine:
v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@yourdomain.com; pct=25Phase 3: Reject (p=reject) Once confident in your setup, enforce full protection:
v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com; pct=100We've found this phased approach prevents legitimate email disruption while building comprehensive protection.
Step-by-Step SPF Setup Guide
Quick Answer: Setting up SPF requires identifying all servers that send email for your domain, creating a properly formatted DNS TXT record, and configuring appropriate failure policies. Most businesses can complete SPF setup in 15-30 minutes through their domain registrar's DNS management interface.
Step 1: Identify Email Sources
Before creating your SPF record, catalog every service that sends emails on your behalf:
Common email sources:
- Primary email provider (Google Workspace, Microsoft 365)
- Marketing platforms (Mailchimp, Constant Contact)
- CRM systems (Salesforce, HubSpot)
- E-commerce platforms (Shopify, WooCommerce)
- Monitoring services (server alerts, uptime monitors)
- SMTP relay services (SMTP2Go, SendGrid)
Documentation tip: Create a spreadsheet listing each service and its required SPF inclusion or IP addresses. This prevents overlooking legitimate sources.
Step 2: Build Your SPF Record
Start with the version tag and add mechanisms for each email source:
v=spf1 include:_spf.google.com include:servers.mcsv.net ip4:192.168.1.10 ~allSPF record construction rules:
- Always start with
v=spf1 - List mechanisms in order of preference
- Use
include:for established providers - Use
ip4:orip6:for specific IP addresses - End with an "all" qualifier (
~allrecommended)
Step 3: Validate and Deploy
Before publishing, validate your SPF record:
Validation tools:
- Google Admin Toolbox MX Lookup
- Dmarcian SPF Survey tool
- DNS lookup commands (
dig TXT yourdomain.com)
DNS implementation:
- Access your domain registrar's DNS management
- Create or modify the TXT record for your root domain
- Add your SPF record as the value
- Set TTL to 3600 seconds (1 hour)
- Save and verify propagation
⚠️ Critical Limitation: According to Dmarcian's SPF documentation, SPF records are limited to 10 DNS lookups. Exceeding this limit causes authentication failures, so consolidate includes where possible.
SPF Troubleshooting
Common SPF errors:
- Multiple SPF records (only one allowed per domain)
- Exceeding 10 DNS lookups
- Incorrect syntax (missing quotes, wrong qualifiers)
- Overly permissive policies (
+all)
Testing methodology:
- Send test emails from each authorized source
- Check email headers for SPF results
- Review any failures with your DNS configuration
- Monitor authentication reports for issues
At Groupmail, we simplify this process by providing clear SPF requirements for our SMTP integrations. When you connect with SMTP2Go, for example, you'll add include:spf.smtp2go.com to enable our 10,000 free monthly emails offer.
Step-by-Step DKIM Setup Guide
Quick Answer: DKIM setup involves generating a public-private key pair, publishing the public key in your DNS as a TXT record, and configuring your email server to sign messages with the private key. Most email providers handle the technical implementation automatically once you add the DNS record.
Step 1: Generate DKIM Keys
Most email providers generate DKIM keys automatically:
For Google Workspace:
- Sign in to Google Admin Console
- Navigate to Apps → Google Workspace → Gmail → Authenticate email
- Click "Generate new record" for your domain
- Copy the provided DNS record information
For Microsoft 365:
- Access the Microsoft 365 Admin Center
- Go to Settings → Domains → Select your domain
- Navigate to DNS records and locate the DKIM CNAME records
- Note the provided CNAME values for DNS setup
For custom implementations: Generate 2048-bit RSA keys using OpenSSL:
bash
openssl genrsa -out private.key 2048
openssl rsa -in private.key -pubout -out public.keyStep 2: Configure DNS Records
DKIM records use a specific naming convention:
[selector]._domainkey.[domain]Example DKIM DNS record:
- Type: TXT
- Name:
jan2025._domainkey.yourdomain.com - Value:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC...
DKIM record components:
v=DKIM1- Required version tagk=rsa- Key type (RSA standard)p=- Base64-encoded public keyh=sha256- Hash algorithms (optional)s=email- Service types (optional)
Step 3: Enable DKIM Signing
After publishing DNS records, activate DKIM signing:
Google Workspace activation:
- Return to Gmail authentication settings
- Click "Start authentication" for your domain
- Verify the status shows "Authenticating email"
Microsoft 365 activation:
- Use PowerShell with Exchange Online commands:
powershell
New-DkimSigningConfig -DomainName yourdomain.com -Enabled $trueThird-party providers: Most ESPs activate DKIM automatically after DNS verification. Check your provider's documentation for specific steps.
Step 4: Verify DKIM Implementation
Test DKIM functionality thoroughly:
Verification methods:
- Send test emails and examine headers for
DKIM-Signature: - Use online DKIM validators with your domain
- Check authentication results in email headers
- Review DMARC reports for DKIM alignment
🔧 Technical Insight: According to RFC 6376, DKIM signatures remain valid even when emails are forwarded, unlike SPF which breaks during forwarding. This makes DKIM crucial for mailing lists and email forwarding scenarios.
Header analysis example:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=yourdomain.com;
s=jan2025; h=from:subject:date:message-id; bh=47DEQpj8HBSa+/TImW+5JCeuQeRkm5NMpJWZG3hSuFU=;
b=signature_data_hereWhen implementing email authentication with Groupmail, our platform works seamlessly with your DKIM setup. Whether you're using our SendGrid integration or the SMTP2Go connection that includes 10,000 free monthly emails, proper DKIM signing ensures your campaigns maintain excellent deliverability.
Step-by-Step DMARC Setup Guide
Quick Answer: DMARC setup requires having functional SPF and DKIM records, then creating a DMARC policy DNS record that specifies how to handle authentication failures. Start with a monitoring policy (p=none), analyze reports for several weeks, then gradually enforce stricter policies to protect your domain.
Prerequisites for DMARC
Before implementing DMARC, ensure you have:
- Functional SPF record with proper mechanisms
- Active DKIM signing for your primary email sources
- Report analysis capability (mailbox or service to receive reports)
- Understanding of your email ecosystem (all legitimate senders identified)
Step 1: Create Initial DMARC Record
Start with a monitoring-only policy to gather data:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.comDNS record configuration:
- Type: TXT
- Name:
_dmarc.yourdomain.com - Value: Your DMARC policy string
- TTL: 3600 seconds
Step 2: Analyze DMARC Reports
DMARC reports provide crucial insights into your email authentication:
Aggregate reports (RUA) arrive daily and include:
- Total message volume
- SPF and DKIM authentication results
- Source IP addresses sending from your domain
- Policy application results
Forensic reports (RUF) provide detailed information about individual authentication failures:
- Complete message headers
- Specific failure reasons
- Sender identification data
Report analysis tools:
- Commercial services (Dmarcian, Valimail, PowerDMARC)
- Open-source parsers (Parsedmarc, DMARC analyzer)
- Manual analysis using spreadsheet tools
Step 3: Progressive Policy Enforcement
Phase 1: Monitor (p=none) Duration: 2-4 weeks
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:forensic@yourdomain.comAnalysis tasks:
- Identify all legitimate email sources
- Resolve SPF and DKIM authentication issues
- Document any unexpected senders
Phase 2: Quarantine (p=quarantine)
Duration: 2-4 weeks
v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@yourdomain.com; pct=25Gradual enforcement:
- Start with 25% policy application (
pct=25) - Monitor user complaints and delivery issues
- Increase percentage weekly (25% → 50% → 75% → 100%)
Phase 3: Reject (p=reject)
v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com; pct=100Final verification:
- Ensure 100% of legitimate email passes authentication
- Monitor for any residual delivery issues
- Document your DMARC deployment for future reference
📊 Implementation Success: Mailgun's 2025 deliverability report shows that among high-volume senders using DMARC, approximately 70% have implemented effective policies, significantly improving their email security posture.
Advanced DMARC Configuration
Subdomain policies:
v=DMARC1; p=reject; sp=quarantine; rua=mailto:dmarc-reports@yourdomain.comIdentifier alignment:
v=DMARC1; p=reject; adkim=s; aspf=s; rua=mailto:dmarc-reports@yourdomain.comFailure reporting options:
v=DMARC1; p=reject; rua=mailto:dmarc-reports@yourdomain.com; fo=1DMARC Troubleshooting
Common implementation challenges:
Legitimate email failures:
- Review SPF record for missing sources
- Verify DKIM signing covers all email streams
- Check for forwarding scenarios that break SPF
Report volume management:
- Use commercial services for large-scale report processing
- Implement automated parsing and alerting
- Archive reports for compliance and analysis
Policy conflicts:
- Coordinate with IT teams managing different email services
- Document exceptions and special handling requirements
- Plan key rotation and maintenance schedules
Our experience at Groupmail shows that DMARC deployment success depends heavily on thorough preparation and gradual enforcement. When you use our platform with properly configured authentication, you'll see improved deliverability rates and greater protection against domain spoofing attempts.
Advanced Email Authentication Strategies
Quick Answer: Advanced email authentication involves optimizing record configurations, implementing automated monitoring, coordinating multiple email sources, and maintaining security through regular key rotation. Enterprise deployments require careful policy management, comprehensive reporting analysis, and integration with existing security infrastructure.
Multi-Domain Authentication Management
Large organizations often manage multiple domains requiring coordinated authentication strategies:
Domain hierarchy considerations:
- Parent domain policies (
p=reject) - Subdomain-specific policies (
sp=quarantine) - Brand protection domains (
p=rejectwith no legitimate email) - Regional domain variations
Centralized policy management:
v=DMARC1; p=reject; sp=none; rua=mailto:dmarc@company.com;
ruf=mailto:forensic@company.com; pct=100; ri=86400Authentication Alignment Optimization
Strict vs. Relaxed alignment:
| Alignment Type | SPF Setting | DKIM Setting | Impact |
|---|---|---|---|
| Relaxed | aspf=r | adkim=r | More permissive |
| Strict | aspf=s | adkim=s | Maximum security |
Relaxed alignment allows subdomain matching (email from mail.company.com passes for company.com) Strict alignment requires exact domain matching for authentication success
Key Rotation and Security Maintenance
DKIM key rotation schedule:
- Generate new keys monthly or quarterly
- Maintain previous keys for 30 days minimum
- Use automated key management where possible
- Document rotation procedures for team consistency
SPF record optimization:
- Regularly audit included mechanisms
- Remove obsolete email sources
- Consolidate includes to stay under 10 DNS lookups
- Monitor for new services requiring authentication
🔧 Enterprise Insight: According to Validity's DMARC analysis, only 8% of analyzed domains have valid DMARC records, highlighting the competitive advantage of proper implementation for businesses.
Automated Monitoring and Alerting
Report analysis automation:
- Parse DMARC reports automatically
- Alert on authentication failures exceeding thresholds
- Track policy compliance across domain portfolio
- Generate executive dashboards showing authentication health
Integration with security tools:
- SIEM integration for threat detection
- Incident response workflows for spoofing attempts
- Threat intelligence feeds for known bad actors
- Compliance reporting for regulatory requirements
At Groupmail, we understand the complexity of enterprise email authentication. Our platform integrates seamlessly with existing authentication infrastructure, whether you're using our analytics dashboards to monitor delivery performance or connecting with external SMTP providers that require specific authentication configurations.
Key Terms
DKIM (DomainKeys Identified Mail): Cryptographic email authentication using public-key signatures to verify message integrity and sender authenticity
SPF (Sender Policy Framework): DNS-based authentication listing IP addresses authorized to send email from a domain
DMARC (Domain-based Message Authentication, Reporting and Conformance): Policy framework combining SPF and DKIM to instruct receivers how to handle unauthenticated emails
DNS TXT Record: Domain Name System text record storing authentication policies and public keys for email verification
Email Spoofing: Fraudulent practice of sending emails with forged sender addresses to deceive recipients
Authentication Alignment: DMARC requirement ensuring the From address domain matches SPF or DKIM authenticated domains
Selector: DKIM identifier enabling multiple authentication keys per domain for key rotation and provider separation
Policy Enforcement: DMARC instruction (none/quarantine/reject) telling receivers how to handle authentication failures
Aggregate Reports: Daily DMARC reports summarizing authentication results and policy applications across all received messages
Forensic Reports: Detailed DMARC reports providing specific information about individual authentication failures
Frequently Asked Questions
How long does email authentication setup take? Basic SPF, DKIM, and DMARC implementation typically takes 2-4 hours spread across several weeks. SPF and DKIM setup require 30-60 minutes each, while DMARC deployment follows a phased approach over 6-8 weeks for optimal safety and effectiveness.
What happens if I configure email authentication incorrectly? Incorrect authentication can cause legitimate emails to be marked as spam or rejected entirely. This is why we recommend starting with DMARC's monitoring policy (p=none) to identify issues before enforcement. Always test with small email volumes first and monitor authentication reports closely.
Do I need all three protocols or can I implement them separately? While SPF and DKIM can function independently, DMARC requires both for maximum effectiveness. Google and Yahoo now mandate DMARC for bulk senders, making all three protocols essential for reliable email delivery to major providers.
How do email authentication protocols affect deliverability? Proper authentication significantly improves deliverability. Studies show that domains with DMARC policies enjoy higher trust ratings from email providers, leading to better inbox placement rates and reduced spam filtering.
Can email authentication prevent all phishing attacks? Email authentication prevents domain spoofing but doesn't stop all phishing. Attackers can still use similar-looking domains or compromised legitimate accounts. Authentication should be part of a comprehensive security strategy including user education and advanced threat protection.
What should I do if my DMARC reports show authentication failures? First, verify the failures aren't from legitimate sources you missed during initial setup. Check if any email services or applications send on your behalf without proper SPF inclusion or DKIM signing. For persistent unknown failures, consider they may be spoofing attempts, which validates your DMARC protection.
How often should I review and update authentication records? Review DMARC reports weekly during initial deployment, then monthly for ongoing monitoring. Update SPF records whenever you add new email services. Rotate DKIM keys every 6-12 months for security. Annual comprehensive audits ensure your authentication remains effective as your email ecosystem evolves.
Is email authentication required for all domain types? While not legally required for most domains, authentication is essential for business credibility and deliverability. Even domains not actively used for email should implement SPF records with "-all" policies to prevent spoofing. NIST recommends authentication for all domains as cybersecurity best practice.
Secure Your Email Communications Today
Implementing DKIM, SPF, and DMARC isn't just about technical compliance—it's about protecting your brand, securing your communications, and ensuring your messages reach their intended recipients.
We've guided you through the complete implementation process, from basic SPF records to advanced DMARC policies. The key to success lies in methodical deployment, careful monitoring, and gradual policy enforcement.
Your next steps:
- Audit your current email sources and identify all services sending from your domain
- Implement SPF records for immediate IP-based protection
- Configure DKIM signing to ensure message integrity
- Deploy DMARC gradually starting with monitoring, progressing to enforcement
- Monitor reports consistently and adjust policies based on real-world data
Remember, email authentication is an ongoing process, not a one-time setup. Regular monitoring and maintenance ensure continued protection against evolving threats.

Start creating professional email campaigns with Groupmail's free account—no credit card required. Access unlimited sending and our live AI subject line generator today.




